Trusted data access
CipherStash makes sensitive data accessible only to the right people at the right time. Implement robust data security with zero functional trade-offs and minimal integration effort.
Why CipherStash
What can you do with trusted data access?
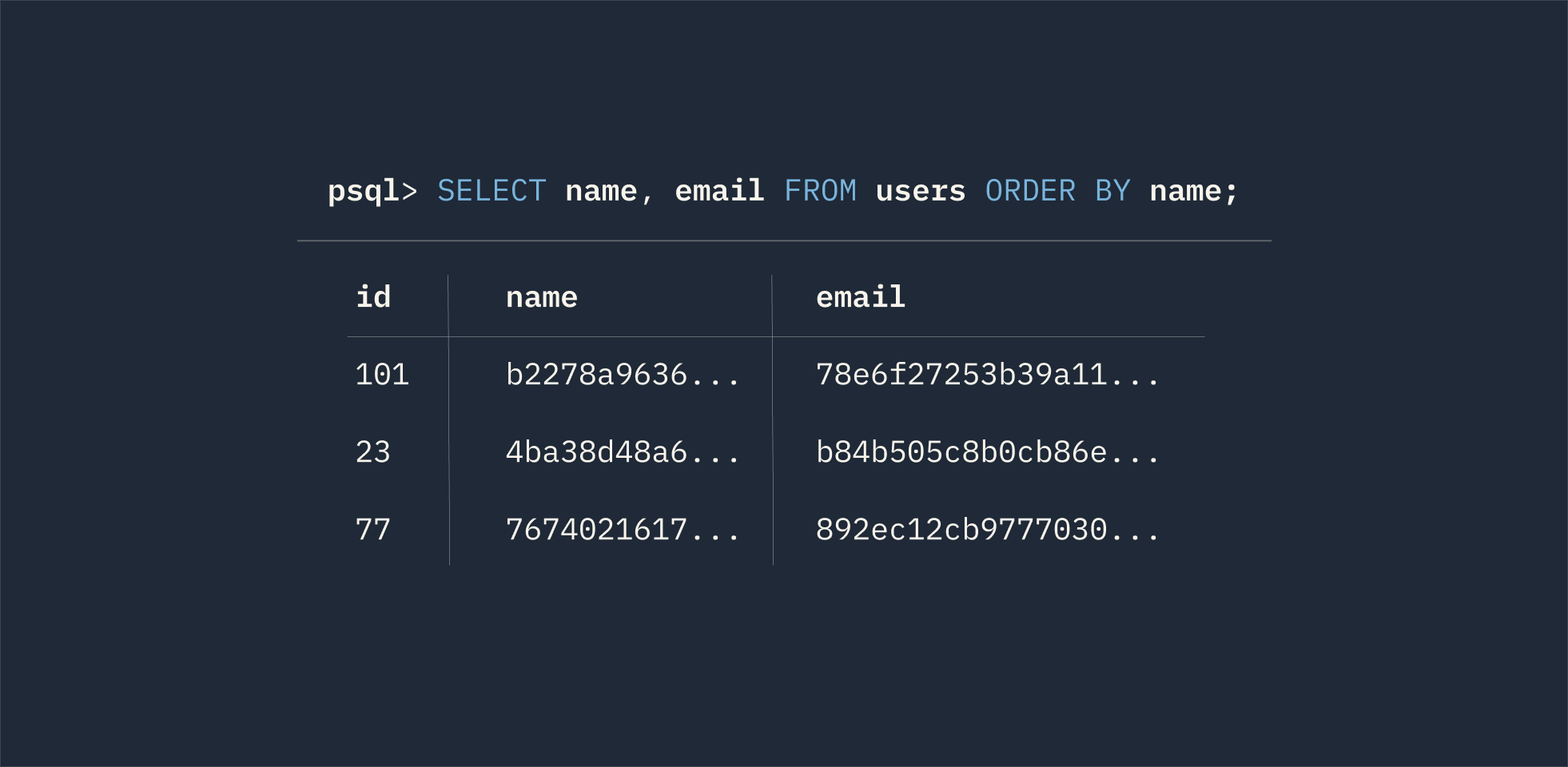
Encryption in use
Store and use customer data with confidence
Your data stays encrypted even when it is in use. Open up new possibilities for customer value by keeping data secure but still searchable and usable.
Identity based
Control access to your data
Whether users are internal or external, your sensitive data stays protected. Grant access by scoping permissions down to individual pieces of data - provable with cryptography.
Audit trail
Demonstrate compliance
Be confident about your data security and privacy. Prove that you're protecting data - the control becomes the evidence you need.
Performance
Encryption that works at scale
ZeroKMS runs in CipherStash cloud with multi-AZ and multi-region failover ensuring high availability and low latency.

Encryption in use enables trusted data access.
Encryption in use keeps data encrypted even while it's queried in the database.
Works in any environment
Our encryption is based on industry standard primitives like AES and SHA2 and rigorously tested.
Zero functional trade-offs
Full-text search, semantic search, range queries, and sorting all work over encrypted data. No features are broken.
Minimal deployment complexity
Integrate CipherStash based on your existing workflows. ZeroKMS runs in CipherStash cloud with multi-AZ and multi-region failover.
Preserve all integrations
Third-party integrations continue to work seamlessly. Offline processes and async workflows remain unchanged. Selective encryption and just-in-time decryption ensure everything keeps working.
Built-in audit trail
Every data access is automatically logged. No need for complex telemetry collection. Prove compliance and track usage with built-in audit capabilities.
Security that closes deals
See how CipherStash helps companies secure their data and close deals.

CipherStash enabled us to achieve the same stringent level of encryption without needing to implement custom envelope encryption using AWS KMS or similar technologies.
Health tech
Read the case study →
With CipherStash, we were able to implement end-to-end encryption while maintaining full search functionality across our entire platform.
Financial services
Read the case study →Integrating CipherStash
Works with your existing tech stack
All our integrations are source-available.
So what makes CipherStash encryption different?
We built ZeroKMS to work with modern applications.
Unique key per value
We built our own key management solution, ZeroKMS, which supports bulk operations to provide a unique data key for every record.
Resilient and secure
With over 3 years of R&D, we've solved a lot of problems because cryptography is hard. We've made it easy to use encryption in your applications.
Searchable encryption
CipherStash encryption is designed to preserve critical functionality like full-text search, semantic search, and third-party integrations while keeping data secure.
Start protecting your data
Get started by creating a free account and choosing your integration path, or get in touch to learn more.