Encryption-in-Use
Safeguard data with searchable encryption
Cipherstash is not encryption just at-rest or in-transit, it's end-to-end, searchable, traceable encryption-in-use.
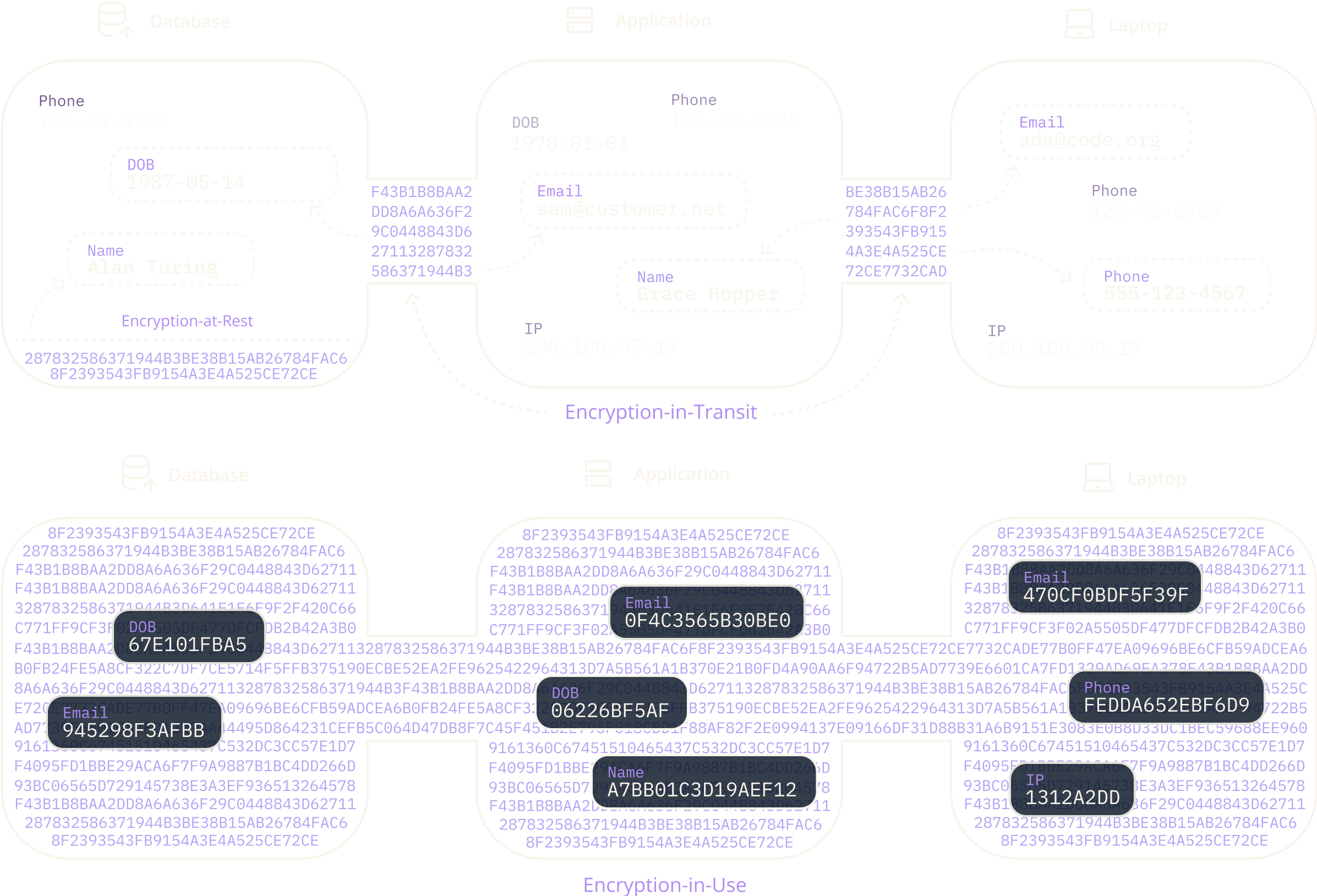
Apply access control directly to your data with encryption-in-use that works everywhere,
from SQL to Spreadsheet.

Cipherstash is not encryption just at-rest or in-transit, it's end-to-end, searchable, traceable encryption-in-use.

Eliminate weak links with precise, consistent, and universally applicable access control and encryption that binds to your data across systems.
Identity-based authorisation checks for every data access attempt ensuring granular control, accurate auditing, and maximum visibility.
Monitor data access to uncover anomalies. Alert and react to stop potential data breaches.

The CipherStash platform incorporates several groundbreaking products that work together to protect your data.
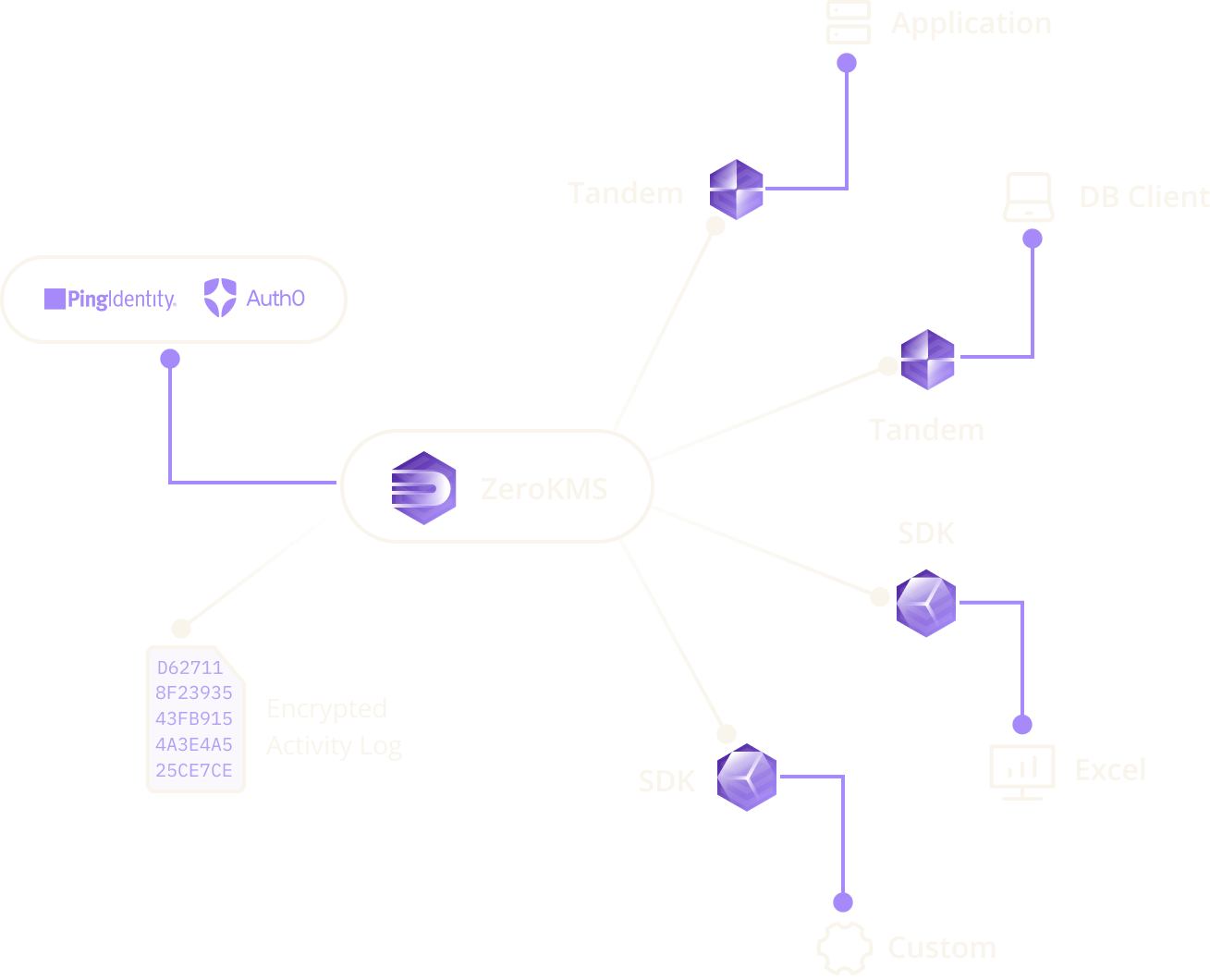
Key management ready for a zero trust future.
Fast and secure, ZeroKMS is the CipherStash key management system, bringing the protection of zero trust to complex data environments where decryption isn’t just done on the server but in the app, in the browser or on the desktop. Designed so that neither the client nor the server needs to be fully trusted, ZeroKMS nullifies the security risks present in traditional trust-based key management.
Encryption-in-Use for any database or warehouse. No code required.
A high-performance searchable encryption proxy that truly works out of the box, requiring no changes to your apps, codebase or data analysis workflows. Ready for deployment at scale with full PostgreSQL support and beta support for SQL Server.
Data governance dashboard for your entire data estate.
Give your administrators and analysts total visibility and control over the who, what and when of your data. Command brings together auditing, policy management, anomaly detection, alerting and logging, allowing you to gain critical data governance insights.
A four step approach to data loss prevention in today's complex threat landscape.
Download the WhitepaperMeet stringent data safety standards and enhance HIPAA compliance without slowing down engineering and data science teams.
CipherStash is deployable on-prem to support banking and financial services organisations with data protection, access control, auditing, and regulatory compliance.
Your customers' data is your business. CipherStash gives your customers the ultimate reassurance that their marketing and transactional data is kept safe throughout its entire lifecycle.
This is what people are saying about CipherStash.
Had a great chat this arvo with @danieldraper about @cipherstash. If I was founding something new today I'd be super duper likely to use this to replace my "user.[rb|ts]" I love how it gives you a PII vault but with flexibility around querying.

If you store PII and tell me it's safe cause you encrypt data at rest, and in transit, you're wrong. If your app or DB is compromised your reputation is in the 🗑. @cipherstash - an end-to-end secure, searchable, performant database. Their infra, your keys. Get on it.

I am still on a high after talking with @danieldraper and @auxesis yesterday. The stuff they are building at @cipherstash is incredible. Making it trivial to do field level encryption in any DB is one thing. But making it still possible to do a full text search is quite another

If you can't find what you're looking for, email our support team and someone will get back to you shortly.
For now, yes though we have several more integrations in the works including AWS Redshift, Microsoft SQL and Google BigQuery.
Encryption-in-Use hides data until an authorized user needs to access it, reducing the risk of unauthorized access. CipherStash's unique key for every field in every record allows for precise permission control, and the key server logs every access for auditing and quick issue resolution.
Yes! PostreSQL hosted in AWS, Azure and Google Cloud are all supported. In fact, any PostgreSQL database later than 14.0 will work.
Never. CipherStash uses searchable encryption which means that both data and queries are encrypted in the client before reaching the database. Results are returned by using a fast cryptographic compare function on the server which never sees the data.
Book a 30 minute demo to see how CipherStash can solve your data protection challenges.
Book a Demo