ZeroKMS
Zero trust key management
Zero Trust is a fundamental principle of secure-by-default design. However, applying Zero Trust to key management is unexpectedly difficult. Existing solutions reveal either data or keys to intermediaries which forces higher trust requirements for vendors and service providers.
CipherStash's ZeroKMS uses Zero Trust Key Management (ZTKM): key management for the connected digital landscape.
ZeroKMS is a key management system. It is built to be used with CipherStash Proxy, but can also be used with any database or application.
ZeroKMS is a managed service that is highly available and deployed in multiple cloud regions globally. ZeroKMS is deployed as a Docker container, so you can deploy it within your own cloud account or on-prem.
ZeroKMS never sees the plaintext data. When a data key is requested, ZeroKMS generates and returns key seeds to the client to create the data key locally. This significantly reduces attack vectors. This means data keys are never seen by third parties and are never sent across the network.
ZeroKMS does bulk encryption and decryption operations which enables a data key to be generated for every single record in your database — without sacrificing performance.
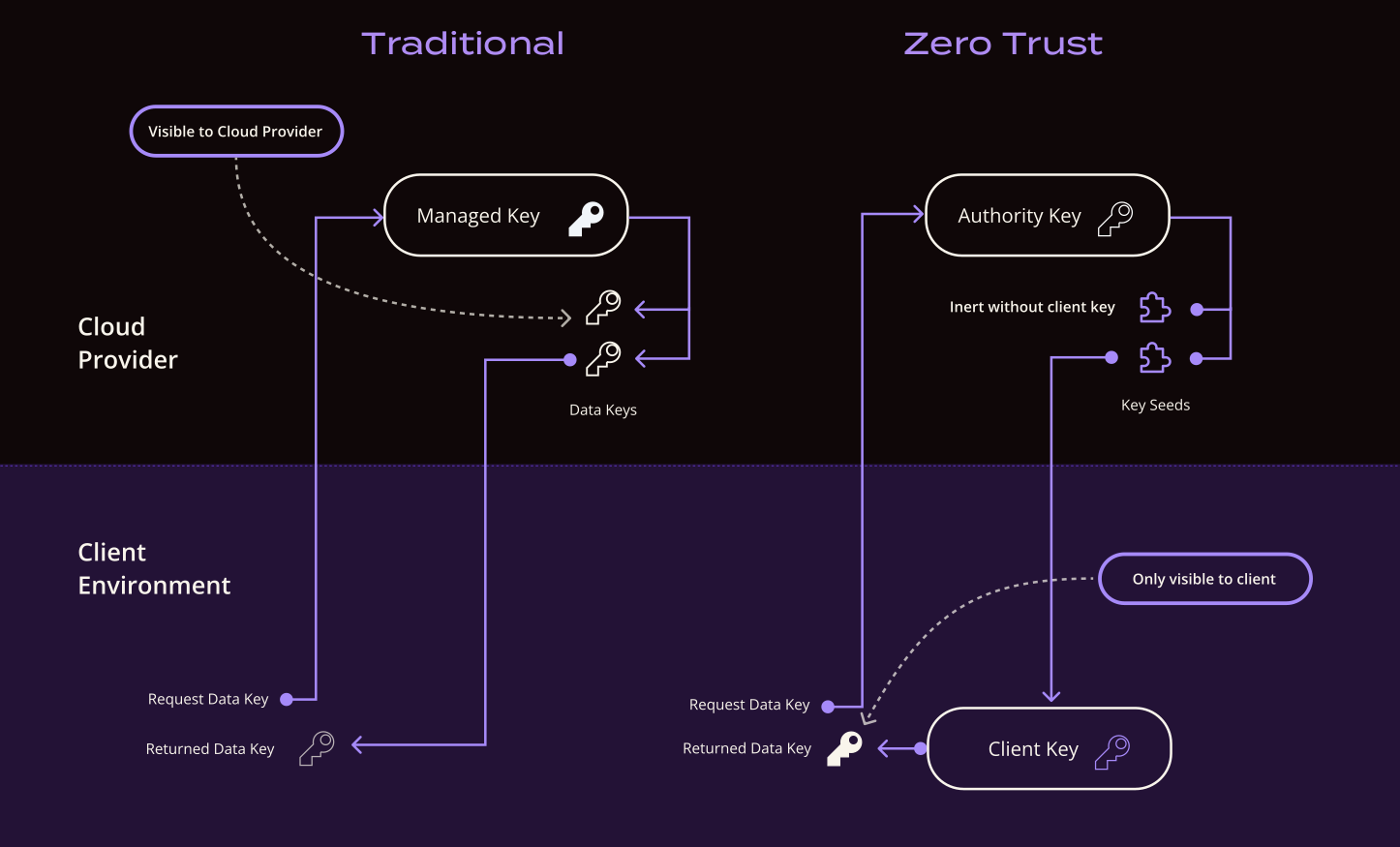
Figure: Traditional KMS vs ZeroKMS
If you'd like to learn more about ZeroKMS, readt the whitepaper on our Trust Center.